Microsoft Security Academy
Are you ready to get started?⏩
Welcome to cybersecurity! Explore our curated resources to help you start your journey.
Start by mastering the basics with Microsoft’s Security 101🎯
Concept Cookbook
| Concept | Description |
|---|---|
| Shared Responsibility Model | Division of security responsibilities between cloud service providers (CSPs) and the customer. |
| AI Shared Responsibility Model | Division of AI security responsibilities between cloud service providers (CSPs) and the customer. |
| Zero Trust | Security model that assumes breaches and verifies each request as though it originates from an open network. |
| Incident Response | Procedures and actions taken to respond to and recover from active attack campaigns. |
| Identity and Access Management (IAM) | Framework for managing identities and access to resources. |
| Identity Protection | The detection, investigation, and remediation of identity-based risks. |
| Multi-Factor Authentication | Authentication method that requires an additional form of identification. |
| Privileged Access | Manages and monitors access to critical resources to prevent unauthorized access. |
| Hardware Security Modules (HSMs) | Physical devices that manage digital keys for strong authentication. |
| Encryption | Process of converting data into code to prevent unauthorized access. |
| Logging or Auditing | Configurable options to generate, collect, and analyze security logs from services. |
| Data Retention | Refers to minimum and maximum timelines for keeping data, including sensitive data, before such data is permanently deleted. |
| Data Loss Prevention | Preventing users from inappropriately sharing sensitive information. |
Product Cookbook
| Feature | Description | Product Page |
|---|---|---|
| Microsoft Sentinel | Scalable SIEM and SOAR for attack detection and incident response. | Microsoft Sentinel |
| Microsoft Defender XDR | Unified pre- and post-breach enterprise defense suite. | Microsoft Defender XDR |
| Microsoft Defender for Cloud | Integrated security monitoring and policy management across multicloud/hybrid. | Microsoft Defender for Cloud |
| Microsoft Entra | Secure access for any identity, from anywhere, to any resource. | Microsoft Entra |
| Microsoft Purview | Unified data security, data governance, and risk and compliance management. | Microsoft Purview |
| Azure Resource Manager | Manages resources as a group with security, auditing, and tagging features. | Azure Resource Manager |
| Azure Monitor | Provides visualization, query, alerting, and automation on Azure data. | Azure Monitor |
| Azure Advisor | Personalized cloud consultant offering security recommendations. | Azure Advisor |
| Web Application Firewall | Protects apps and APIs from common web-based attacks. | Web Application Firewall |
| Azure Key Vault | Manages and secures cryptographic keys and secrets. | Azure Key Vault |
| Azure Backup | Protects assets against ransomware with a centralized backup service. | Azure Backup |
| Azure Site Recovery | Orchestrates replication, failover, and recovery of workloads and apps. | Azure Site Recovery |
Microsoft Zero Trust Architecture
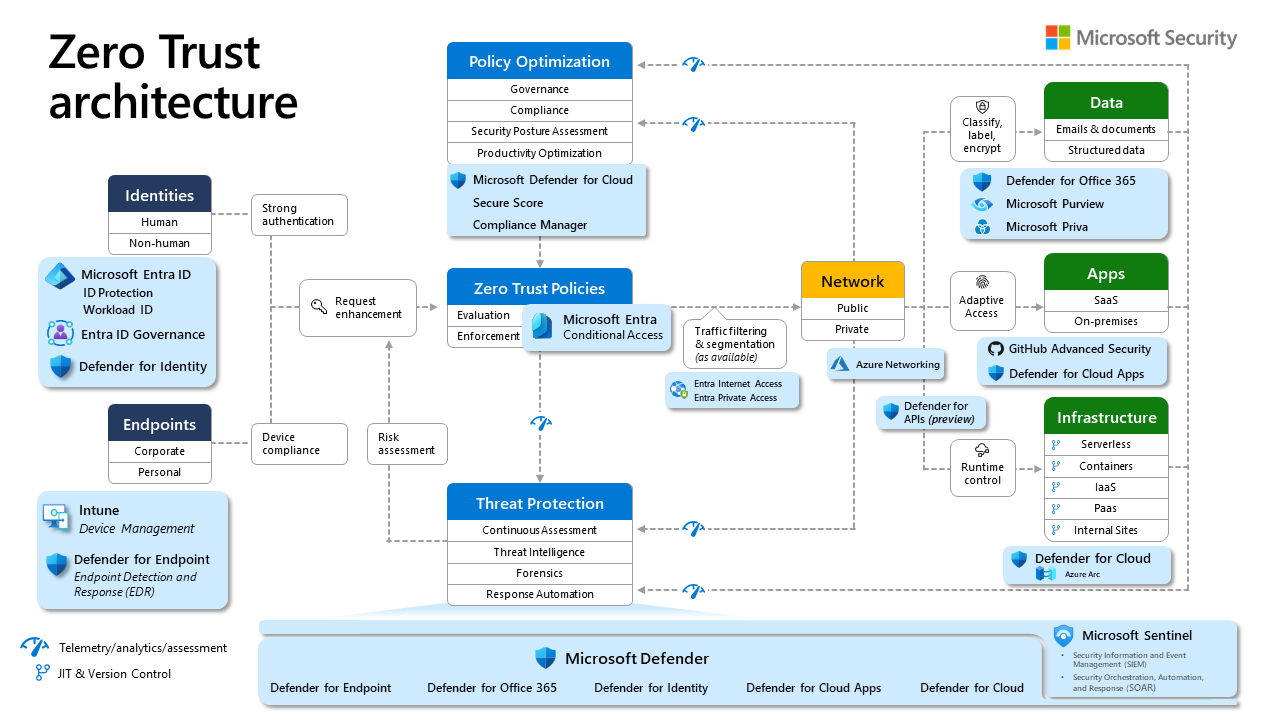
Security Strategy
- NEW: Learning for Microsoft Cybersecurity Architects
- Define a Security Strategy
- Microsoft Cybersecurity Reference Architectures
Zero Trust
Security Operations Analyst
- NEW: Learning for Microsoft SOC Analysts
- Security Operations (SecOps) Functions
- What is Microsoft Sentinel?
- What is Microsoft Defender XDR?
- What is Microsoft Defender for Cloud?
- What is Microsoft Defender for Endpoint?
Identity and Access Administrator
- NEW: Learning for Microsoft I&A Admins
- What is Azure Active Directory (Microsoft Entra ID)?
- What is Entra ID Protection?
- What is Microsoft Entra ID Governance?
- What is Global Secure Access?